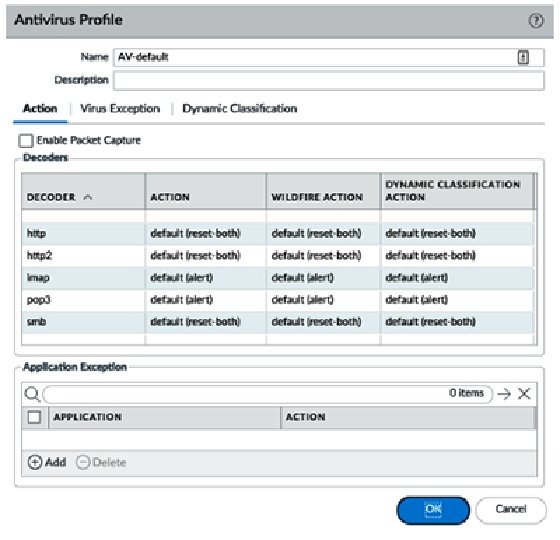
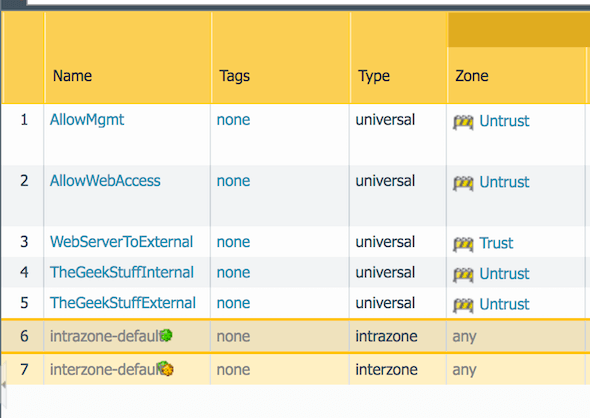
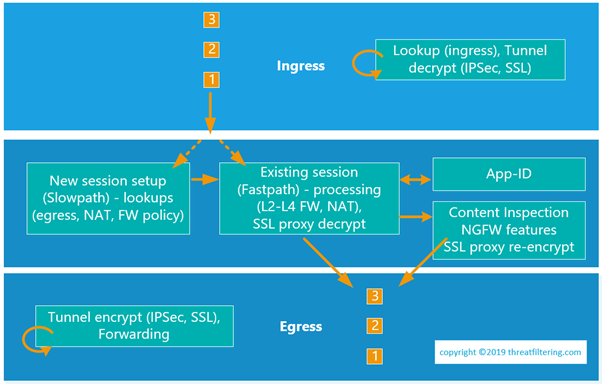
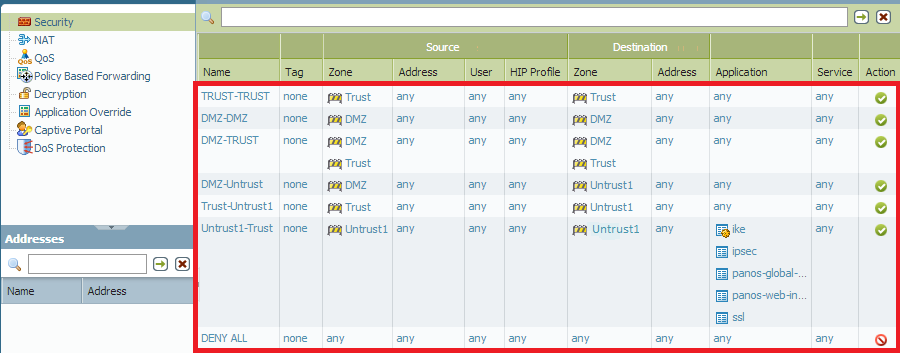
Palo Alto tip: If you create tags with the names of your interfaces and give them nice colors, your security and NAT policies look like this : r/sysadmin
How to See Traffic from Default Security Policies in Traffic Lo... - Knowledge Base - Palo Alto Networks
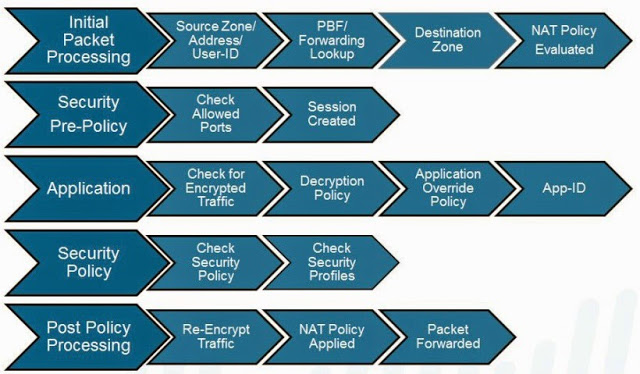
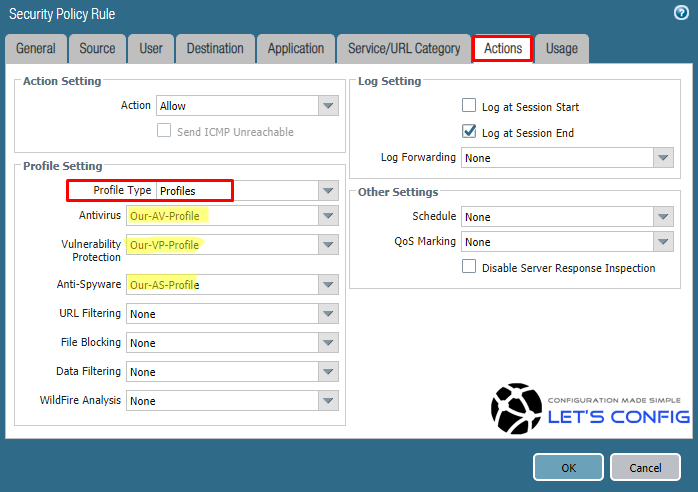


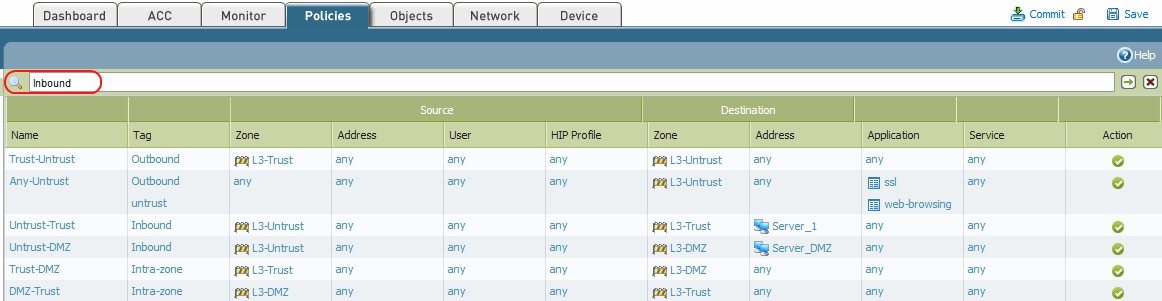

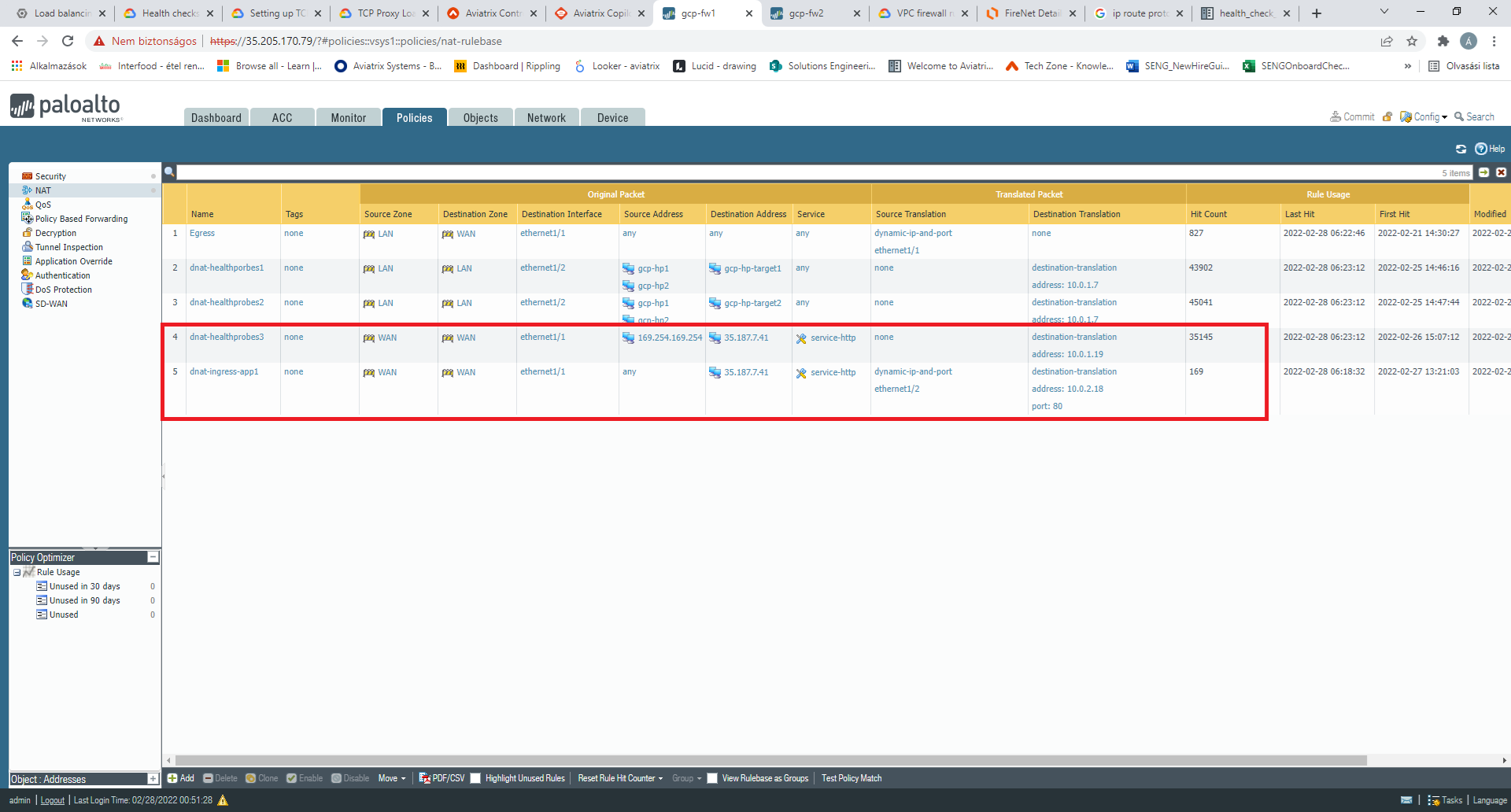
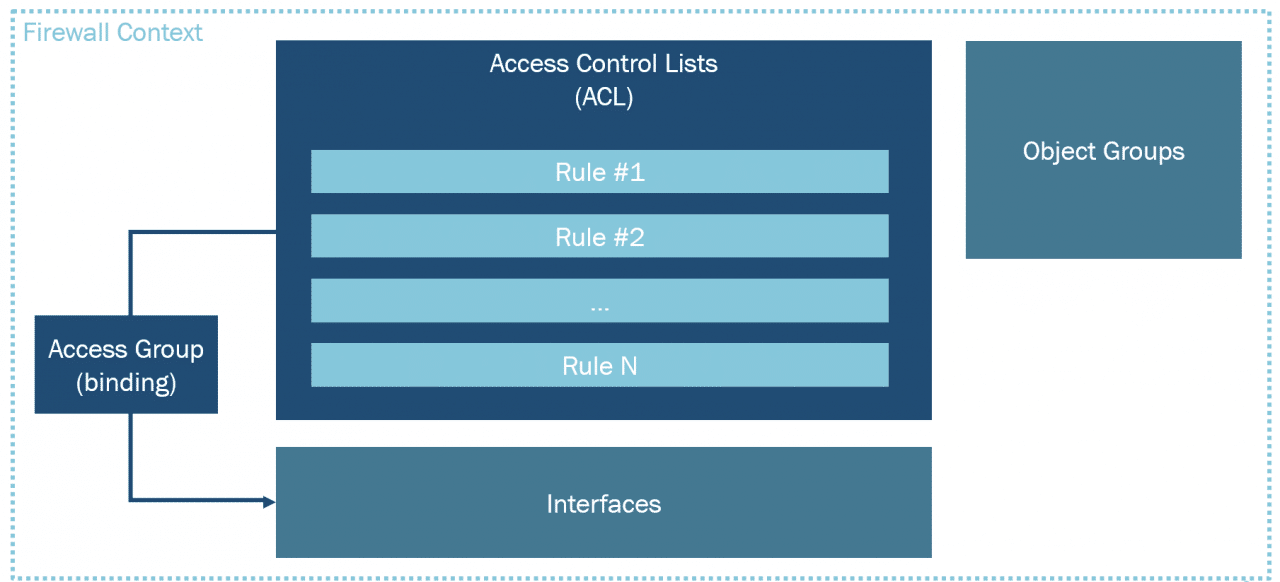

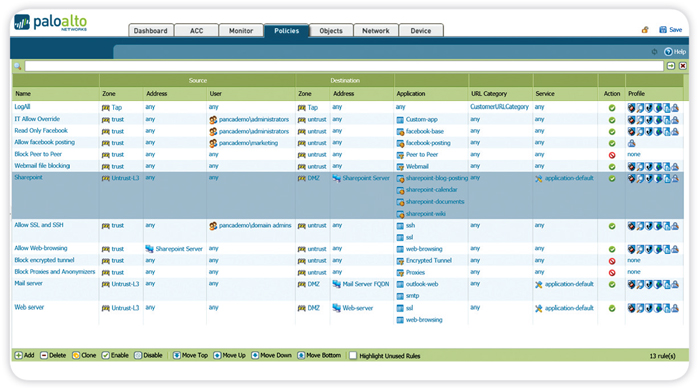
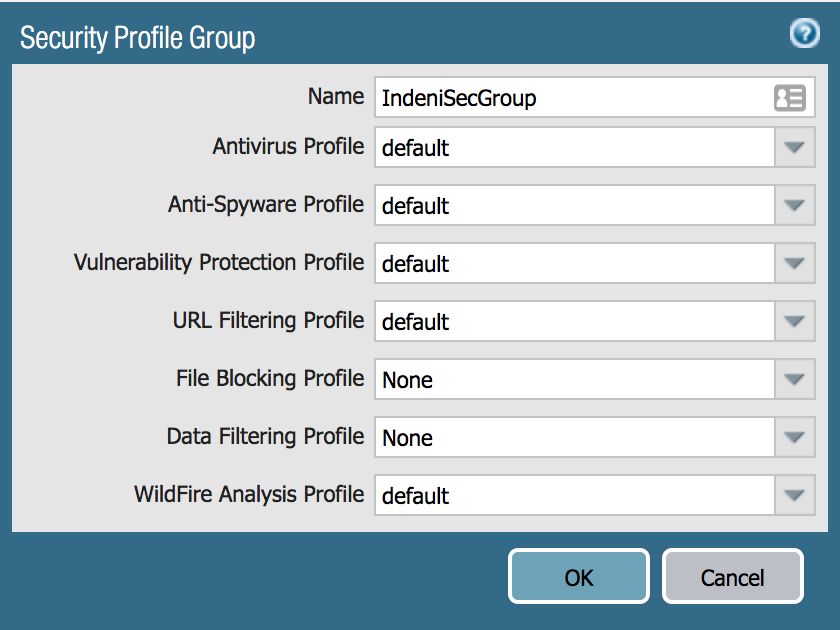
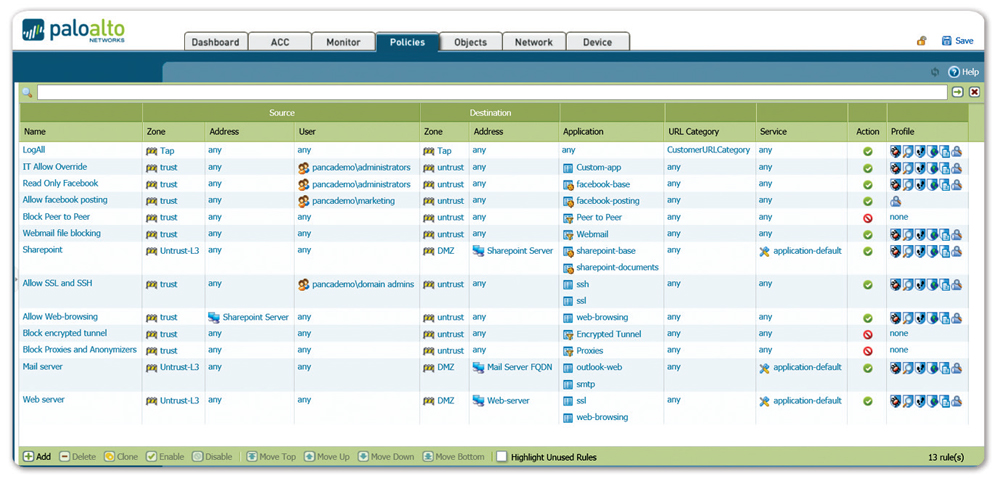
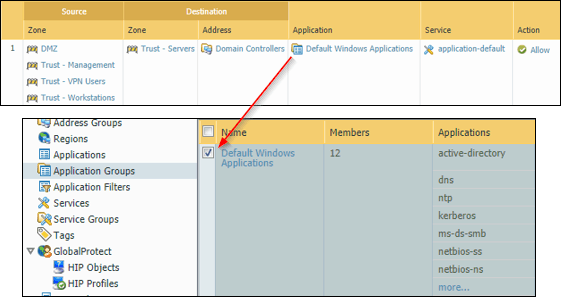

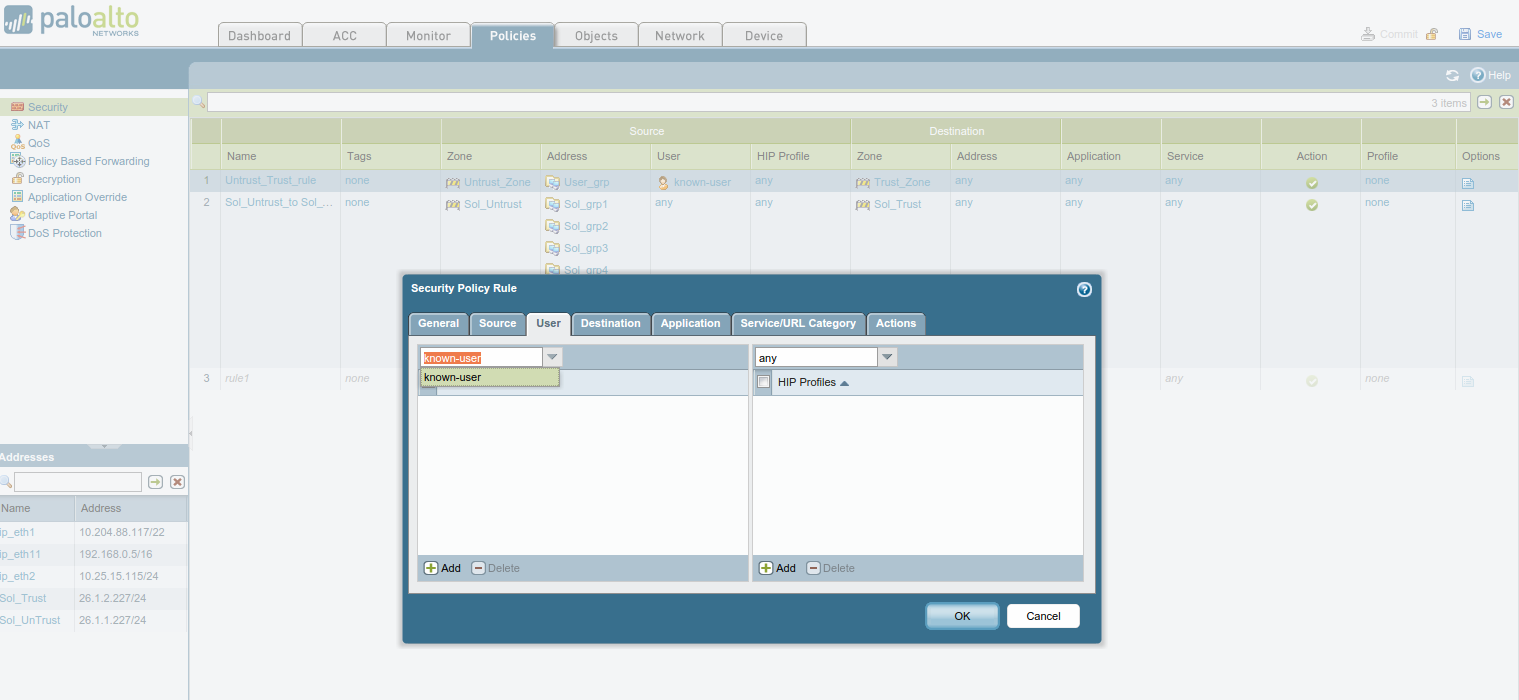


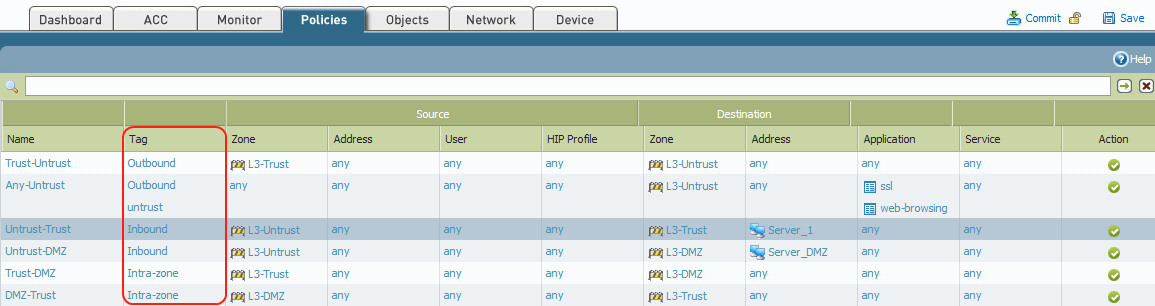
![Python]Adding firewall rules to Palo Alto using PA REST API – cyruslab Python]Adding firewall rules to Palo Alto using PA REST API – cyruslab](https://cyruslab.files.wordpress.com/2017/12/snip20171205_14.png)